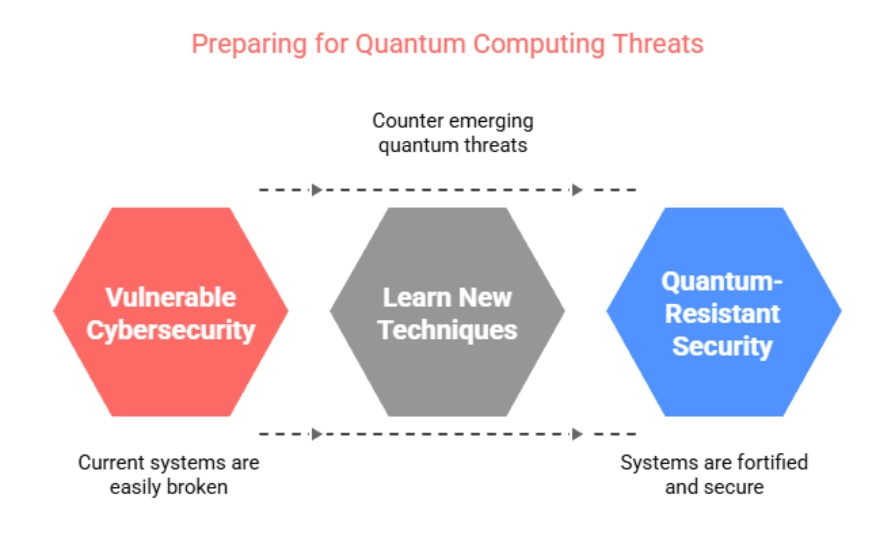
Quantum computing isn’t science fiction anymore. It’s quickly moving from labs into real-world use and is already starting to impact industries like healthcare, finance, and logistics. But as the technology grows, so do quantum computing threats, creating a new layer of cybersecurity concerns for businesses and governments alike.
The problem is that most of today’s encryption methods weren’t built to handle the speed and power of quantum computers. These machines can solve problems much faster than regular computers, which could make many current security systems easier to break.
That’s why ethical hackers need to start thinking ahead. The tools and techniques that work today might not be enough tomorrow. Taking a certified ethical hacking course can help security professionals build the mindset and skills needed to counter emerging quantum threats.
In this blog, you’ll learn about five serious threats that quantum computing brings to cybersecurity and how you can start preparing to deal with them.
1. The Fall of RSA and ECC Encryption
Modern cybersecurity relies heavily on RSA and ECC encryption. These systems protect everything from your messages to your banking data. But quantum computers can crack these algorithms exponentially faster than classical computers.
- RSA, which could take thousands of years to break with current systems, could fall in minutes to a powerful enough quantum machine.
- ECC, often used in blockchain and secure apps, is just as vulnerable.
How you can counter this:
- Start learning about post-quantum cryptography, a new class of encryption methods designed to withstand quantum attacks.
- Ethical hackers should explore algorithms like Lattice-based cryptography and Hash-based cryptography to test for quantum-resistant security.
- Practice vulnerability testing on systems using outdated encryption, many still use RSA with no transition plan in place.
2. Quantum Speedups in Password Cracking
Brute force attacks are painfully slow with traditional tools. But with quantum computing’s Grover’s algorithm, these attacks become much more efficient.
- Grover’s algorithm can reduce the time needed for brute-force attacks by a square root factor.
- That means a password that takes years to break today could be cracked in hours with quantum.
What you can do as an ethical hacker:
- Focus on stronger password hashing algorithms like Argon2 or bcrypt, which are tougher even under quantum conditions.
- Test systems for outdated hashing methods like MD5 or SHA1, they’re already weak and won’t survive in a quantum world.
- Recommend longer, more complex passphrases, not just complex characters. Length becomes more important than ever.
3. Quantum Attacks on Blockchain Systems
Blockchains are often seen as secure by design. But they heavily depend on cryptographic algorithms that are vulnerable to quantum threats.
- Digital signatures (used in crypto wallets and transactions) can be forged by quantum machines.
- If quantum computers reach sufficient power, they could theoretically reverse blockchain transactions or drain wallets.
Here’s how you can respond:
- Analyze blockchain platforms for their digital signature mechanisms, ECDSA and RSA need to go.
- Start experimenting with quantum-secure blockchain protocols, like those using XMSS or Lamport signatures.
- Simulate attacks using ethical hacking tools to show how current systems would behave under a post-quantum scenario.
4. Spoofing and Interception of Quantum Communications
Quantum communication promises unhackable transmissions, but only under ideal conditions. Real-world quantum communication systems, especially in early deployment, can have flaws.
- Side-channel attacks and system misconfigurations can expose sensitive quantum data.
- The complexity of quantum channels also makes them vulnerable to spoofing during deployment.
How you can stay ahead:
- Learn to test quantum key distribution (QKD) setups for real-world weaknesses.
- Explore device-level vulnerabilities, not just the theory, most errors don’t come from the algorithm, but the implementation.
- Stay informed on standards being developed for secure quantum communication protocols.
5. Nation-State Quantum Surveillance
Governments and large institutions are already investing billions in quantum research. That means surveillance tools are also going quantum.
- Massive data centers might already be storing encrypted data for future decryption once quantum power arrives.
- Once operational, these systems could breach old archives of emails, documents, and even VPN tunnels.
How ethical hackers can respond:
- Raise awareness about forward secrecy, which ensures that past sessions remain secure even if long-term keys are compromised.
- Encourage organizations to adopt quantum-safe VPNs and messaging apps.
- Simulate nation-state-level surveillance threats to help companies visualize risks and tighten their policies.
How You Can Start Preparing Now
Quantum threats aren’t just something to worry about in the future. The shift is already happening. Some of the systems we use today could become vulnerable the moment large-scale quantum computers go live. That’s why now is the time to prepare.
As an ethical hacker, you have the opportunity to be part of the solution. You can help shape how cybersecurity adapts in a post-quantum world. Here’s how to start:
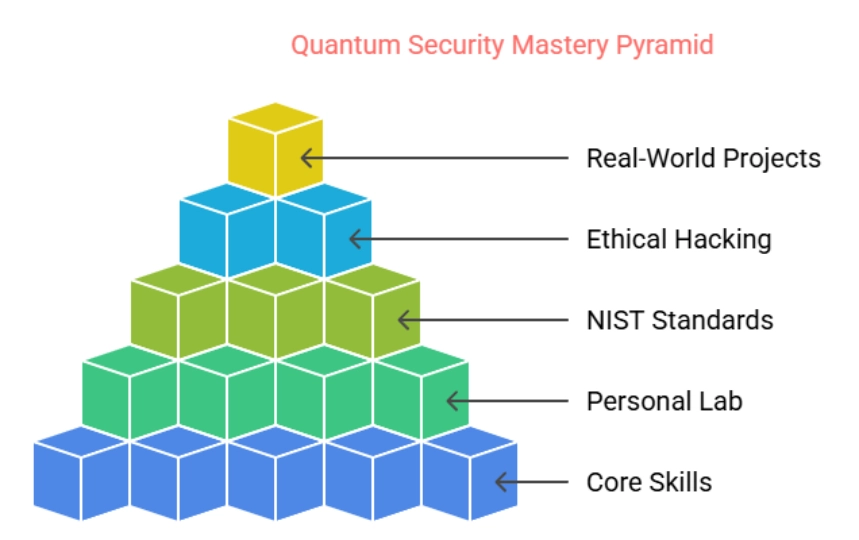
- Build a personal lab and experiment with quantum-safe cryptography
Set up a test environment on your local machine or a cloud platform. Try implementing post-quantum algorithms like CRYSTALS-Kyber or SPHINCS+. These are designed to resist quantum attacks and are part of the algorithms being reviewed by global standards bodies. Practice testing for weaknesses and learn how these new systems behave under pressure. - Stay updated with NIST’s post-quantum standards
The National Institute of Standards and Technology (NIST) is working with researchers around the world to define which encryption algorithms will protect our data in the future. Their recommendations are already shaping how companies and governments prepare. Keeping up with these updates will give you an edge and help you understand what’s coming before it hits the mainstream. - Join ethical hacking communities focused on quantum security
Communities like forums, Discord groups, or GitHub projects often share the latest tools, research, and experiments. By contributing or even just observing, you’ll get valuable insight into how other ethical hackers are approaching these challenges. It’s a great way to learn, get inspired, and collaborate on solutions that haven’t been invented yet. - Focus on core skills that remain relevant
Quantum computing may change the landscape, but skills like secure coding, penetration testing, and understanding network protocols are still essential. Build your foundation and then layer quantum knowledge on top of it. The stronger your base, the better prepared you’ll be. - Create real-world projects that test post-quantum ideas
Try building a simple encrypted chat app using quantum-safe algorithms. Or audit a sample blockchain implementation for quantum vulnerabilities. Hands-on projects like these not only improve your skills but also demonstrate your understanding to potential mentors or employers.
Preparing for quantum computing isn’t just about learning new tools. It’s about thinking differently. The systems of tomorrow won’t be protected by the same rules as today, so now’s your chance to get ahead of the curve.
Appin Can Help You Stay Ahead
Quantum computing may change the rules, but ethical hackers can write the new playbook. Appin helps you stay a step ahead by offering advanced training, real-world labs, and community support focused on future-ready cybersecurity.
Whether you’re learning ethical hacking or diving into quantum-safe cryptography, Appin gives you the tools, mentors, and environment to sharpen your skills for what’s next.
Your next opportunity in cybersecurity isn’t just about keeping up, it’s about staying ahead. Appin is here to help you do exactly that. Enquire Now to find the right program for your learning goals.


