Kali Linux scenarios often start with real-world breaches, like uncovering a misconfigured firewall that exposed sensitive data. If you’ve ever asked “what is Kali” and why it’s the go-to pentesting distro, you’re in the right place. This post walks through five common Kali Linux scenarios used by ethical hackers.
Here’s what we’ll cover:
- Network Discovery and Scanning: Mapping active hosts and open ports
- Web Application Testing: Intercepting and probing web traffic
- Wireless Network Assessments: Capturing and cracking Wi-Fi handshakes
- Password Cracking: Using tools to test password strength
- Forensics and Data Recovery: Recovering deleted files and building timelines
By exploring these scenarios, you’ll see how Kali Linux tools turn theory into practice. Understanding these workflows prepares you for hands-on exercises and helps you decide if ethical hacking is the right path for your cybersecurity career.
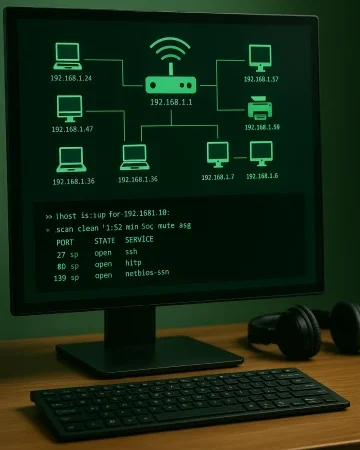
Scenario 1: Network Discovery and Scanning
Mapping a live network is the first step in many Kali Linux scenarios. You need a clear picture of active hosts and services before moving on to deeper tests. With the right tools, you can automate this process and uncover targets efficiently.
Key tools for network discovery:
- Nmap for comprehensive port and service scans
- Netdiscover for quick ARP-based host detection
Basic steps to follow:
- Run a host discovery scan
- Use nmap -sn 192.168.1.0/24 to list all active devices on the subnet
- Identify open ports and services
- Run nmap -sV 192.168.1.10 to see which ports are open and what applications are running
These simple scans give you a map of the network landscape. From there, you can plan targeted vulnerability assessments or move on to web and wireless testing. Mastering these steps sets the foundation for more advanced ethical hacking workflows.
Scenario 2: Web Application Testing
Web applications often suffer from vulnerabilities like SQL injection, cross-site scripting, and insecure configurations. Testing these requires reliable ethical hacking tools. Kali Linux packages everything you need to probe and protect web apps.
Key tools for web testing:
- Burp Suite Community Edition for intercepting and modifying HTTP requests
- Nikto for quick automated scans of web servers
- OWASP ZAP for in-depth passive and active vulnerability analysis
A simple workflow to follow:
1. Intercept requests in Burp Suite
- Configure your browser proxy to Burp and explore the application
- Modify parameters to test for injection or authentication bypass
2. Run an automated Nikto scan
- Execute nikto -h http://target.com to find outdated software and common issues
3. Verify findings with OWASP ZAP
- Use ZAP’s active scan to confirm vulnerabilities and view detailed reports
This sequence shows how Certified Ethical Hacking professionals approach web assessments. You start with manual exploration, then automate checks, and finally validate results. Mastering these steps in Kali Linux ensures you cover the most critical web weaknesses and can provide clear remediation advice.
Scenario 3: Wireless Network Assessments
Wireless networks in offices and public spaces are tempting targets. Weak encryption, default settings, and open hotspots can expose sensitive data. Kali Linux scenarios often include testing Wi-Fi security to close these gaps.
Key tools for wireless assessments:
- Aircrack-ng suite for capturing and cracking encrypted handshakes
- Reaver for testing WPS pin vulnerabilities
Essential steps to follow:
1. Capture a WPA2 handshake
- Put your wireless adapter into monitor mode with airmon-ng start wlan0
- Use airodump-ng wlan0mon to list nearby networks and capture the handshake
2. Crack the handshake with Aircrack-ng
- Run aircrack-ng -w /path/to/wordlist.txt capture.cap to test passwords against the captured handshake
3. Test WPS via Reaver
- Execute reaver -i wlan0mon -b [BSSID] -vv to attempt a WPS PIN attack
By running these tests, you identify weak encryption and misconfigured WPS settings. This workflow shows how ethical hackers use Kali Linux scenarios to secure wireless environments and protect users from common network attacks.
Scenario 4: Password Cracking
Passwords remain a common entry point for attackers when they are weak or reused. Ethical hacking tools help you test these credentials before someone else does. Kali Linux includes powerful programs for this purpose.
Key tools for password cracking:
- John the Ripper for straightforward wordlist and rule-based attacks
- Hashcat for GPU-accelerated cracking of complex hashes
Example commands to try:
Basic John the Ripper wordlist attack
john –wordlist=/usr/share/wordlists/rockyou.txt hash.txt
- This command tests each word in the list against the hashes in hash.txt.
GPU-accelerated cracking with Hashcat
hashcat -m 0 -a 0 hash.txt /usr/share/wordlists/rockyou.txt
- Here, -m 0 specifies MD5 hashes and -a 0 selects a straight attack mode using your GPU for faster results.
Running these commands shows how quickly weak passwords fall. You can then recommend stronger policies or multi-factor authentication. By mastering these ethical hacking tools, you protect systems from common credential attacks and improve overall security posture.
Scenario 5: Forensics and Data Recovery
After a security incident, you need to uncover what happened and restore lost data. Kali Linux scenarios include forensic investigations that recreate events and recover evidence. Two key tools make this process smoother: Autopsy and Foremost.
Tasks to perform in post-incident analysis:
1. Recover Deleted Files with Foremost
- Run foremost -i disk-image.dd -o output_folder to scan a disk image for known file headers
- Review recovered documents, images, and archives in the output folder
2. Build a Timeline in Autopsy
- Launch Autopsy and create a new case pointing to your disk image or directory
- Use the Timeline view to map file creation, modification, and access events
- Examine keyword hits and extracted artifacts for evidence of malicious activity
These steps help you piece together attacker actions, from the first intrusion to data exfiltration. Foremost digs out deleted evidence, while Autopsy organizes findings into a clear sequence.
By practicing these workflows in Kali Linux scenarios, you sharpen your ability to respond to breaches and support incident reports. Mastering forensic and recovery tools ensures you can both trace attack paths and restore critical information, making you a valuable asset in any cybersecurity team.
Why Kali Linux for Ethical Hackers
Kali Linux is the preferred platform for ethical hacking because it comes ready with hundreds of security tools. You don’t need to hunt for or install individual programs. The distribution is fully customizable and can run in live-boot mode, letting you test environments without altering host systems.
Key advantages of Kali Linux:
1. All-in-One Distribution for Pentesting
- Includes tools for scanning, exploitation, forensics, and more
2. Regular Updates and Community Support
- Official releases keep tools current and secure
- A large community shares tutorials, plug-ins, and best practices
3. Ease of Setting Up Lab Environments
- Run Kali from a USB drive or virtual machine with minimal configuration
- Snapshots and rollbacks help you reset after tests
Because Kali Linux bundles essential ethical hacking tools in one OS, you save time on setup and focus on learning. Live-boot flexibility means you can carry a portable lab in your pocket. Regular updates ensure you use the latest versions of tools like Nmap, John the Ripper, and Burp Suite.
Conclusion and Next Steps
Mastering Kali Linux scenarios, such as network scanning, web testing, wireless audits, password cracking, and forensics, gives you practical skills for real-world security work. Each workflow moves you beyond theory and into hands-on problem solving.
Key takeaways:
- Build a clear map of network assets and services
- Identify and exploit common web vulnerabilities
- Expose weak Wi-Fi configurations before attackers do
- Test password strength and recommend stronger policies
- Recover deleted data and reconstruct incident timelines
Ready to practice these scenarios in a guided lab environment? Inquire now to explore Appin Indore’s Certified Ethical Hacking course and get expert feedback on your work.