Why do cybersecurity beginners misuse key terms?
Many beginners misunderstand cybersecurity terms, using them interchangeably without realizing how different they actually are. These small mistakes can cause big confusion during interviews, certification exams, or team discussions.
Clear understanding of common cybersecurity terms helps you sound professional and build accurate knowledge. This blog will explain 17 commonly misused words and their correct meanings, so you can use them with confidence in your career and training.
1. What is the difference between a virus and malware?
A virus is a type of malware, but not every malware is a virus.
Malware refers to any malicious software designed to harm systems, while a virus specifically spreads by attaching itself to other files.
Common types of malware include:
- Trojan – hides within legitimate software
- Ransomware – locks your data for payment
- Spyware – secretly collects your information
Understanding this difference helps you correctly identify threats during cybersecurity analysis or lab sessions.
2. Is hacking always illegal?
No, hacking is not always illegal. It depends on intent and permission.
Ethical hacking involves testing systems legally to find and fix vulnerabilities, while illegal hacking exploits weaknesses for harm or profit.
The main categories include:
- White hat – authorized ethical hackers
- Gray hat – semi-legal hackers testing boundaries
- Black hat – criminal hackers causing damage
If you want to pursue this field professionally, joining certified ethical hacking training helps you develop legal and industry-recognized hacking skills.
3. What’s the confusion between encryption and hashing?
Encryption protects data by converting it into unreadable form, which can be reversed using a key. Hashing, on the other hand, is one-way and used for data integrity.
Encryption secures communication such as emails or financial transactions.
Hashing ensures that passwords or files are not altered during storage or transfer.
In cybersecurity, both are essential for data protection, but they serve different purposes, one hides data, while the other verifies it.
4. Are phishing and social engineering the same thing?
Phishing is just one type of social engineering attack.
Social engineering manipulates people into revealing information, while phishing specifically uses fake emails, messages, or websites to trick users.
For example:
- A fake email claiming to be from your bank is phishing.
- Convincing someone to share credentials in person is social engineering.
- Both rely on human psychology, making awareness and verification your first defense.
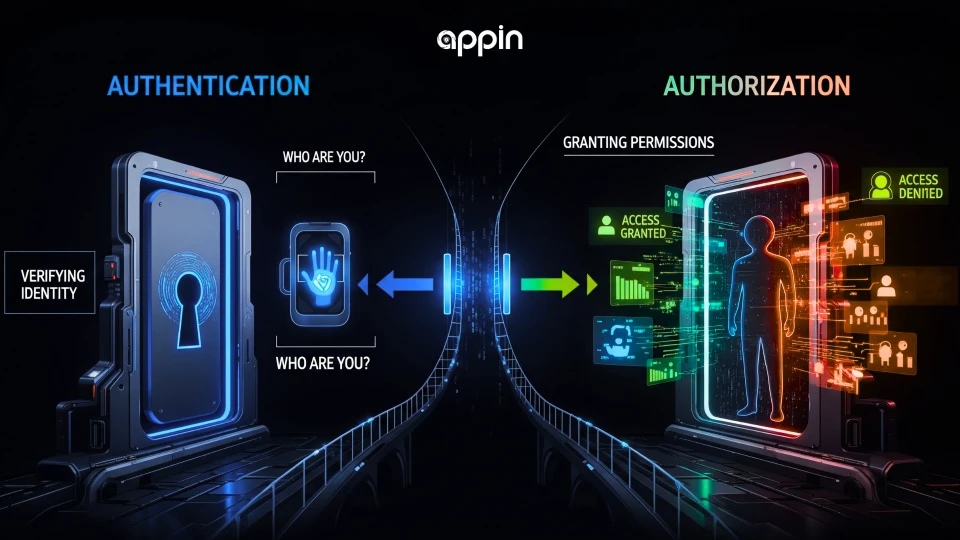
5. What’s the difference between authentication and authorization?
Authentication confirms who you are, while authorization determines what you can do.
When you log into a system, authentication verifies your identity through passwords or OTPs.
Once verified, authorization grants access to specific files or actions based on your role.
A simple analogy: scanning your ID to enter a building is authentication, but being allowed into certain rooms is authorization. Both processes protect data in secure systems.
6. Do firewalls and antivirus software do the same job?
No, firewalls and antivirus software perform different but complementary functions.
A firewall acts as a filter that blocks suspicious traffic from entering your network.
An antivirus detects and removes malicious software already inside your system.
Think of a firewall as a security guard at the gate and antivirus as the cleaning crew inside. Using both together strengthens system protection.
7. Why do people confuse white hat, gray hat, and black hat hackers?
The confusion comes from misunderstanding hacker categories based on intent.
White hats work legally to improve security.
Gray hats explore vulnerabilities without malicious intent but often without permission.
Black hats act illegally to exploit systems.
Each type reflects a hacker’s ethics and goals. Learning these distinctions through certified ethical hacking training prepares students to become skilled white hat professionals.
8. Are vulnerability and exploit the same?
No, a vulnerability is a weakness, while an exploit is the technique used to take advantage of it.
A vulnerability could be outdated software or weak passwords.
An exploit is the code or method attackers use to breach that weakness.
Understanding both terms is vital in security testing. Programs like Appin’s bug bounty diploma program help students identify vulnerabilities safely and ethically in real lab environments.
9. What’s the confusion between DDoS and DoS attacks?
Both attacks overload systems, but they differ in scale.
A DoS (Denial of Service) attack comes from one source, while a DDoS (Distributed Denial of Service) uses multiple compromised systems to flood a target.
Example:
- DoS = one person calling your phone repeatedly.
- DDoS = hundreds calling at once to crash your line.
This distinction helps cybersecurity analysts plan stronger defense strategies.
10. What does brute force really mean in cybersecurity?
A brute force attack involves guessing passwords repeatedly until one works.
Attackers use automated tools to test thousands of combinations per second.
This technique is common when passwords are weak or reused.
To protect against it, cybersecurity professionals recommend strong passwords, two-factor authentication, and lockout policies after failed login attempts.
11. Are cookies dangerous for users?
Cookies are not inherently dangerous, but some can affect privacy.
Functional cookies remember user preferences and login sessions, improving browsing convenience.
However, tracking cookies collect browsing data for marketing or analytics, which can feel intrusive.
Deleting cookies regularly and managing permissions helps maintain better web security and privacy.
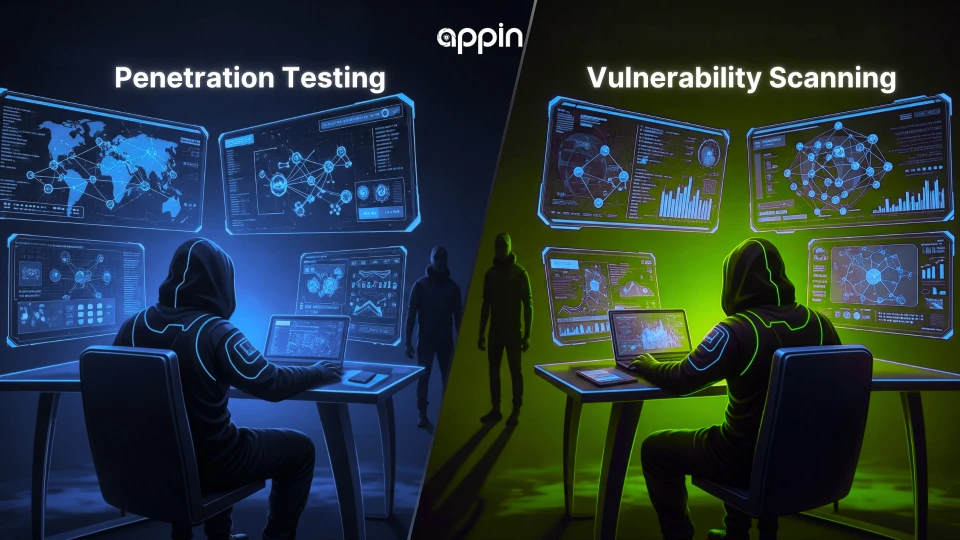
12. Is penetration testing the same as vulnerability scanning?
No, penetration testing goes deeper than vulnerability scanning.
A vulnerability scan uses automated tools to detect known weaknesses.
Penetration testing involves manual testing by professionals who simulate real attacks to evaluate system defense.
Appin’s CEH v13 AI-powered course trains students in both, combining automation with hands-on ethical hacking skills for career growth.
13. Why is “zero-day” often misunderstood?
A zero-day exploit targets a vulnerability before developers know or can fix it.
This makes it highly dangerous, as there is no patch or defense available yet.
Zero-day attacks are often used against major organizations and governments.
Learning about zero-day response and patching processes is crucial for ethical hackers and security analysts.
14. Do SSL and HTTPS mean the same thing?
They are related but not identical.
HTTPS is the secure version of HTTP that ensures data is safely transmitted online.
It uses SSL (or its updated version, TLS) to encrypt communication between browser and server.
When you see a padlock in your browser, it means SSL or TLS is active, making the connection secure.
15. What does patch management actually involve?
Patch management means updating software to fix vulnerabilities and performance issues.
It includes identifying missing patches, testing them, and applying updates safely.
Neglecting patch management leaves systems open to known attacks.
Regular patching is a key part of cybersecurity maintenance across all organizations.
16. What’s the real meaning of sandboxing?
Sandboxing creates a safe environment to test programs without harming your system.
It isolates files or applications, allowing security teams to observe their behavior.
If the software is malicious, it stays contained inside the sandbox.
This method helps analysts detect and study new threats safely.
17. Why does misusing these terms hurt your career?
Incorrect terminology makes you sound inexperienced in cybersecurity discussions.
Recruiters and mentors quickly notice when students misuse basic terms like malware or encryption.
Consistent misuse can reduce your credibility in interviews or practical exams.
Joining verified cybersecurity certification programs helps you learn accurate terminology and build a stronger professional foundation.
What should students remember about using cybersecurity terms correctly?
Using correct cybersecurity terms reflects precision, clarity, and understanding.
It’s not just about memorizing definitions but applying them in real scenarios.
Mastering these terms strengthens your professional image and prepares you for certifications like CEH or Bug Bounty.
If you’re ready to learn cybersecurity concepts the right way, Appin’s certified programs can help you start with confidence.