Imagine your Instagram account got hacked – it’s pretty scary, right? In just a matter of seconds, it could be gone, and getting it back isn’t always guaranteed.
All the hard work you put into building your followers, potential brand deals, and precious memories can be lost in an instant due to a hack. Many people have gone through this, losing everything they worked for on Instagram.
Beyond personal loss, these hacks pose a threat to your followers, with hackers potentially demanding money from them. It’s a serious issue that we’ll navigate together, ensuring you’re armed with the knowledge to protect your account and the community you’ve built.
So, why do hackers target your accounts? How do they actually do it? What happens if your account gets hacked? And most importantly, how can you make sure your Instagram account is safe?
Why hackers hack your Instagram accounts
It’s important to keep your Instagram account safe from hackers. But why would someone want to get into your Instagram account? Well, here are four reasons they might try.
- Spamming for Profit: Hackers may target Instagram accounts to exploit them for sending spam messages. Spam messages can contribute to a company’s profits, as they can boost visibility. However, there are guidelines for direct messages (DMs), and exceeding them could lead to an account ban. Some companies may resort to hiring hackers to gain unauthorized access and maximize their earnings.
- Sale of Hacked Accounts – Stolen Instagram accounts can become commodities in the underground market. Hackers may sell these compromised profiles to individuals or entities seeking to amass a significant follower base quickly. These buyers might exploit the acquired accounts for various purposes, including promotional activities, further complicating the landscape of digital security on the platform.
- Steal your personal data – Your Instagram account holds a lot of information, and hackers can exploit it for their benefit. For instance, they can use your usernames and passwords to access your accounts on other websites. If they get hold of your bank card details, they could spend your money for their own purposes.
- Monetary Extortion – In some cases, hackers may aim to extort money from Instagram account owners. They could access sensitive information, such as compromising photos or private messages, and then threaten to expose or share this content unless a ransom is paid. This malicious tactic preys on the victim’s fear of reputational damage, pushing them to comply with the hacker’s demands.
- Boost other accounts on Instagram – Hackers, or those who’ve hired them, use the hacked accounts to like, repost, and comment on the Instagram pages they want to promote. It’s a way of manipulating engagement and visibility on the platform.
Now, let’s take a look at how your Instagram account can get hacked. Understanding these risks can help you stay safe in the world of social media.
How Does Instagram Account Get Hacked?
Various methods can be employed to hack Instagram accounts. Here are some most common ways:
With the Help of Malicious Software
Hackers can sneak onto your computer using a particular keylogging software program. This program records everything you type, so if you type in your Instagram details, the hacker can grab them. Another way is if you click on a link or download something suspicious, malicious software can get into your computer.
Some sneaky hackers work hard to break into accounts, but the software they use is against the law in most places. Sometimes, the software is fake and tricks people who want to get into someone else’s profile into becoming victims.
Phishing Attacks:
One of the most common methods employed by hackers is phishing. This technique involves tricking users into providing their login credentials through fake login pages or malicious links.
These deceptive pages often mimic the appearance of the official Instagram login, making it challenging for users to discern the fraud. There are also fake websites that pretend to be real. They trick you into giving away your password or making you sign up, saying you’ll get access to specific accounts.
Through Third-Party Apps
Instagram hacks can also happen in a indirectly way. Cybercriminals might target a third-party platform that some people use to get into Instagram, and in doing so, they can compromise all the connected account details.
This can happen through Instagram integrations or linked platforms like Facebook. So, it’s not just about securing your Instagram account directly but also being cautious about the tools or apps connected to it
Brute Force Attacks:
Another way hackers try to break into Instagram accounts is through brute force attacks. It’s not as sneaky, but it can be just as powerful. In this situation, hackers use automated tools to keep trying different combinations of usernames and passwords until they find the right one.
If you use a weak password or one that is commonly used, attackers are more likely to figure it out in this type of attack. So, having a strong and unique password is crucial to protect your account from this kind of hacking attempt.
SIM Card Swapping:
Some hackers use a more advanced technique called SIM card swapping. In this method, they trick mobile service providers into redirecting your phone number to a SIM card they control.
Once they have control, they can use the “Forgot Password” feature to reset your Instagram password and get into your account. It’s a more sophisticated way of hacking that involves manipulating the mobile network to gain access to your account.
Credential Stuffing:
When people use the same login details on different platforms, hackers might use a technique called credential stuffing. This involves using combinations of usernames and passwords that are already known from breaches on other websites.
By doing this, they try to gain unauthorized access to Instagram accounts. So, using unique passwords for each platform is crucial to prevent this type of hacking method.
In-App Scams
Hackers sometimes use scams to trick people into revealing their account details. One common tactic is sending Instagram messages claiming that friends have sent gifts, but the link actually takes people to a fake site that steals their passwords.
In other scams, cybercriminals target Instagram and Facebook users with Cash App scams, promising to send some money. However, falling for these offers could result in identity theft, according to experts. It’s essential to be cautious and verify the authenticity of unexpected messages or offers to avoid falling victim to these scams.
How do I know if my Instagram account has been hacked?
When we mention your Instagram account being hacked or compromised, we mean that someone who is either not you or not authorized by you has gained access to your account without your permission.
The easiest way to tell if your Instagram account has been hacked is if you see any changes that you didn’t make yourself, like:
- Unfamiliar posts: Posts, stories, or reels showing up on your Instagram account that you didn’t create.
- Increased account activity: Messages sent from your account or message threads with people you don’t know.
- Unauthorized changes: Any alterations to your account, like changes to your name, profile picture, description, username, and so on.
- Suspicious login attempts: If you’re getting notifications about login attempts from unfamiliar locations or devices, it indicates someone might be trying to access your account without permission.
- Anonymously Logged Out: If you can’t access your account, a potential reason could be a hacker altering your login credentials.
Beyond the visible alterations, modifications to your account settings can indicate that someone may have hacked your Instagram account. These changes include updates to security settings, the addition of third-party apps, or the inclusion of new phone numbers or email addresses to your account. Some of these adjustments can lead to losing access to your account, making it impossible to log in.
Instagram might proactively contact you if they notice suspicious activity related to your account. For instance, if there are changes to personal information, like the email linked to your account, you might receive an email notification giving you the option to undo the change. Staying alert to such notifications can help you take swift action in case of a potential hack.
How to Protect Your Instagram Account from Hackers
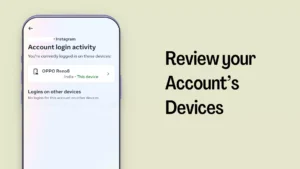
Review your Account’s Devices
In your Instagram settings, you can check which devices are currently logged into your account.
To do this go to profile section > click on 3 lines from the top right hand side > click on settings and privacy > Accounts Centre > Password and Security > Where you’re Logged in.
Take a look at the list of devices and make sure you recognize all of them. If there’s a device you no longer use or don’t recognize, it’s a good idea to log out of it, especially if your account has been compromised recently. Regularly reviewing the devices logged into your account is a smart way to keep your account secure and ensure that no one has unauthorized access.
Pick a Strong Password
Weak passwords are a common way that cybercriminals compromise accounts. It’s crucial to use a strong password for your Instagram, even if it seems tough to remember. A robust password should have at least 16 characters and include a mix of upper and lower case letters, numbers, and symbols.
Avoid reusing passwords or creating variations of them. Reused passwords make you susceptible to credential-stuffing attacks, where a cybercriminal uses one compromised password to access multiple accounts.
If remembering passwords is a challenge, consider using a password manager. This tool will remember all your passwords, store them securely, and generate strong passwords for you. It can also autofill your passwords, making it quick and easy to log in to your Instagram while keeping your account safe.
Use two-factor authentication
Two-factor authentication adds an extra layer of protection to your Instagram account. Here’s how it works: when you log in from a new or unfamiliar device or location, even if someone has your password, they’ll need to verify their identity with a security code.
After selecting an authentication method, the app will give you backup codes in case you can’t access your usual method. It’s a good idea to take a screenshot of these backup codes and store them securely, such as in a password-protected cloud storage service like Google Drive or Dropbox.
This way, if you ever lose access to your usual authentication method, you can still get into your Instagram account using the backup codes.
How to Set-up Two Factor Authentication
To set up two-factor authentication on Instagram, go to profile section > click on 3 lines from the top right hand side > click on settings and privacy > Accounts Centre > Password and Security > two-factor authentication.
In that section you can see two options to choose from: “Authentication App (recommended)” and “Text Message”.
Option #1: Authentication App
If you choose the “Authentication App (recommended)” option for two-factor authentication on Instagram, it involves using a third-party authentication app.
Here’s how it works: If you already have such an app installed, Instagram will automatically detect it and send a code to the app. You’ll then retrieve the code from the app and enter it on Instagram to activate two-factor authentication.
If you don’t have an authentication app installed, Instagram will recommend one for you to download before completing the process. This app will help generate the codes needed for two-factor authentication, adding an extra layer of security to your account.
Option #2: Text Message
If your Instagram account doesn’t have a confirmed phone number, you’ll be prompted to enter one. After entering your phone number, tap the “Next” button.
Once you’ve completed this step, the next time you log into your Instagram account from an unfamiliar device, you’ll receive a security code via SMS. This code serves as an additional layer of security to verify your identity and protect your account from unauthorized access.
Keep your email safe
Securing your email account is just as important if you’re concerned about Instagram security, as your email is the means to reset your Instagram password if needed.
If your email account gets hacked, the hacker can reset your Instagram password and take control of your account. To prevent this, ensure your email account has a strong password and consider enabling two-factor authentication if it’s available.
The steps for enabling two-factor authentication may vary depending on your email service. For example, with Gmail (a popular email service), you can find the option by logging into your Google account and navigating to the “Security” tab. Always prioritize the security of both your email and Instagram accounts to keep your online presence safe.
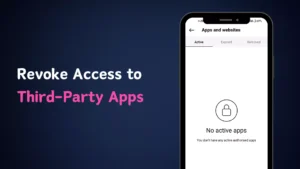
Revoke access to third-party apps
If you’ve ever linked your Instagram account to a third-party app, like a social media management tool or an app for posting directly from your computer, it’s a smart move to revoke its access.
Here’s how: Go to your Profile > Settings and Privacy > Website permissions > Apps and websites.
You’ll see a list of all the apps and websites that have access to your Instagram account. Review the list and revoke access for any apps you no longer use or don’t recognize. Hackers might exploit these third-party apps to gain entry to your account, so it’s a good idea to be cautious and remove access to any that are unnecessary or unfamiliar.
What You Can Do When Your Instagram is hacked?
If you suspect your Instagram account has been hacked, taking prompt steps can help recover and secure it.
If you can still log into your account:
1. Change your password immediately.
- Sign in to your Instagram account.
- Go to Settings and click on “Change Password.”
- Enter your old password and then set a new, secure password.
(Ensure it includes a mix of uppercase and lowercase letters, numbers, symbols, is unique, at least 10 characters long, and not shared with anyone.)
If you can’t sign in:
- Go to the login page and click on “Forgot Password.”
- Follow the prompts to verify your identity and reset your password.
- Ensure the new password meets the secure criteria mentioned above.
Taking these actions promptly helps regain control of your Instagram account and enhances its security.
Check Your Email
If the associated email address of your Instagram account is changed, Instagram will send you an email confirmation. And if you’re unable to log in and suspect hacking, check your inbox for an email from security@mail.instagram.com. If you discover an email from this address indicating a change in your email, you can opt to revert this change to secure your account.
If you haven’t received an email from Instagram or can’t regain access via your email, you’ll need to proceed to the next step in the account recovery process.
Request a Login Link
If you’re unable to regain access to your compromised Instagram account, you can request a login link from Instagram to be sent to your email or phone number. Follow these steps:
Click on either “Get help logging in” or “Forgot password?” (the language may vary based on whether you access Instagram via an Android or iPhone).
- Enter your username, email address, or phone number.
- Opt for either your phone number or email address to receive the login link.
- Click the link sent to your selected option and follow the provided instructions to recover your account.
Request a Security Code
If the link doesn’t work, and you’re still unable to access your Instagram account, you can request a security code. Follow these steps:
- Click the “Need more help?” option when going through the steps to request a login link.
- Choose the option to request a security code.
If, for any reason, you don’t receive a security code, you’ll need to go through the process of verifying your identity to regain access to your Instagram account.
Verify Your Identity
If none of the previously mentioned steps have helped you regain access to your compromised Instagram account, you’ll need to go through the process of verifying your identity.
For a personal account or an account with pictures of you, Instagram will request a video selfie to confirm identity. Submit the video, and Instagram will assess whether it’s sufficient to verify your identity for account recovery. If the initial video fails to confirm your identity, you may need to submit another video.
If your account is a professional one or doesn’t have pictures of you, the verification process involves providing the email address or phone number associated with the account and specifying the type of device used during the account’s creation. Follow the instructions provided by Instagram to complete the identity verification process and regain access to your account.
Can I get my Instagram account back after it’s been hacked?
The short answer: It depends.
The likelihood of recovering your hacked Instagram account depends on how quickly you act and the extent of the changes made by the hacker. If you respond swiftly, you may be able to regain control before the hacker causes significant damage, such as changing your personal data or posting unauthorized content. In such cases, you can avoid the hassle of a lengthy recovery process through Meta support.
However, if the hacker has already made substantial changes, such as altering your password, email, and phone number, the recovery process becomes more challenging. Instagram may assist in recovering your account, depending on the extent of the damage. Unfortunately, if the hacker has deleted your account, the chances of recovery might be limited, and the Instagram support team may face constraints in restoring your account.
Conclusion
The security of your account is paramount in protecting not only your personal information but also the community you’ve built. Hacking poses multifaceted threats, from spamming for profit to personal data theft, and even extortion or rivalry-driven attacks. Understanding the common methods hackers employ, such as malicious software, phishing, or brute force attempts, is essential.
Protect your account through robust measures like strong, unique passwords, two-factor authentication, and vigilant monitoring of third-party apps. In the unfortunate event of a hack, swift action is crucial—change passwords, review account settings, and, if necessary, follow Instagram’s recovery steps. Stay proactive to keep your Instagram haven secure in the dynamic online landscape.
Ready to fortify your digital fortress? Equip yourself with the skills to safeguard not just your Instagram but the entire online realm. Explore the world of ethical hacking through our comprehensive ethical hacking training course. Learn the strategies employed by ethical hackers to thwart cyber threats and protect digital landscapes.