On October 9, 2024, Star Health and Allied Insurance, one of India’s largest health insurance providers, confirmed that it was the victim of a significant cyberattack. The malicious breach resulted in unauthorized and illegal access to sensitive data, leaving millions of Indian customers vulnerable. While the company’s operations remained unaffected, the potential impact of this attack on its customers is alarming.
What We Know About the Star Health Cyber Attack?
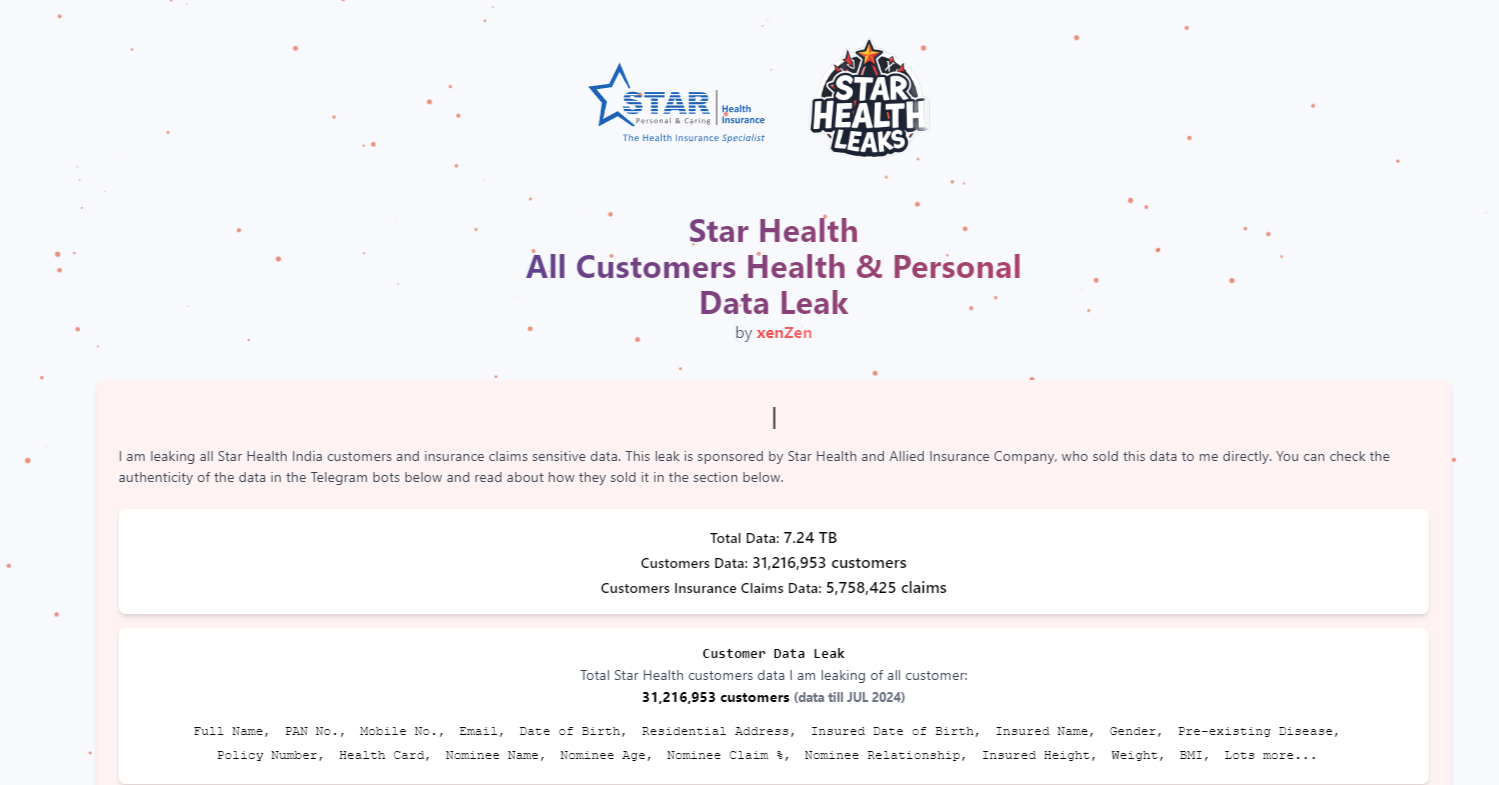
The attack targeted Star Health’s vast database, which includes the personal and medical information of over 17 crore Indians. While investigations are ongoing, reports suggest that hackers made the stolen data publicly accessible through Telegram chatbots. These bots allowed potential buyers to access personal health data, including phone numbers, addresses, tax details, copies of ID cards, medical diagnoses, and more. In total, the data of over 31 million policyholders and information about more than 5.8 million claims were compromised.
The stolen data was initially shared through Telegram bots, which have been used for similar hacks in the past. After the bots were taken down by Telegram, the hackers set up a website selling the data for $150,000. In a shocking revelation, the hackers claimed that Star Health’s chief information security officer had sold the data to them.
Star Health’s Response
Star Health immediately launched a thorough forensic investigation, led by independent cybersecurity experts. The company has also reported the incident to insurance and cybersecurity regulatory authorities, filing a criminal complaint and working closely with government bodies throughout the investigation.
To combat the sale of the stolen data, Star Health has moved the Madras High Court, filing a legal complaint against Telegram for hosting the bots and against Cloudflare, a US-based software company, for hosting the hacker’s website. This legal battle highlights the ongoing complexity of dealing with cybercrimes in an increasingly connected world.
The Importance of Cybersecurity
This attack is a stark reminder of the critical need for robust cybersecurity measures in today’s digital landscape. As more organizations digitize their operations, the risk of cyberattacks increases exponentially. Sensitive data—such as personal identification, medical records, and financial information—is a lucrative target for cybercriminals, making cybersecurity a top priority for every organization, especially those in sectors like healthcare and finance.
For businesses, this means investing in comprehensive cybersecurity frameworks that include:
- Data Encryption: Ensuring that all sensitive data is encrypted both at rest and in transit to prevent unauthorized access.
- Employee Training: Regularly educating employees on cybersecurity risks and best practices to minimize human error, which is often a weak link in security protocols.
- Advanced Threat Detection: Implementing tools that detect unusual activity or potential breaches before they can cause damage.
- Regular Audits and Penetration Testing: Conduct regular audits and simulated attacks to identify vulnerabilities and patch them before hackers can exploit them.
For individuals, this incident highlights the importance of being cautious with their personal information online. Practicing basic cyber hygiene—such as using strong, unique passwords, enabling two-factor authentication, and being vigilant about phishing attacks—can help protect personal data from being compromised.
Conclusion
The Star Health cyberattack serves as a sobering reminder of how vulnerable even large organizations can be to cyber threats. As cybercriminals become more sophisticated, the importance of investing in top-tier cybersecurity measures cannot be overstated. Protecting sensitive data is not just a corporate responsibility—it’s a necessity for maintaining trust and safeguarding the privacy of millions.
Cybersecurity is no longer optional. It is the backbone of the digital world we live in, and failing to prioritize it can lead to devastating consequences for businesses and individuals alike.
Looking for a trusted, comprehensive ethical hacking course? Appin Technology Lab has you covered! Whether you’re a beginner or an experienced professional, our training programs provide clear, accessible instruction across a wide range of ethical hacking topics. With a strong focus on hands-on learning, we ensure you gain the practical skills and expertise needed to excel in the fast-evolving world of cybersecurity. Start your journey with us and become a proficient ethical hacker today!


