Cybersecurity isn’t just essential, it’s booming. As digital threats grow more complex and organizations invest heavily in protection, the demand for skilled professionals has reached an all-time high. For those looking to break into or grow within the industry, exploring the highest paying roles in cybersecurity can offer a clear direction toward both financial and professional advancement. That demand comes with competitive salaries, specialized roles, and clear growth paths.
In 2025, cybersecurity isn’t just about defending systems, it’s about driving strategy, ensuring resilience, and building trust in the digital age. If you’re planning your entry or growth in this field, knowing which roles lead the market in terms of pay and prestige is a smart place to start. Enrolling in a Cyber Security Certification Course can be a key step toward qualifying for these high-demand positions and accelerating your career path.
Here are the top five highest paying cybersecurity roles in 2025, and what it takes to get there.

1. Chief Information Security Officer (CISO)
The CISO stands at the intersection of technology, leadership, and risk. It’s one of the most prestigious and demanding roles in cybersecurity tasked with protecting an organization’s digital ecosystem, shaping its long-term security posture, and navigating complex regulatory landscapes.
This is not a technical role alone. A strong CISO balances deep security expertise with boardroom fluency and operational oversight. They drive cybersecurity not as a cost center, but as a core enabler of business continuity, reputation, and resilience.
- Average Salary (India): ₹65–90 LPA+
- Average Salary (Global): $180,000–$300,000/year
Key responsibilities include:
- Designing and owning the full cybersecurity strategy, from prevention to detection to recovery
- Leading incident response teams and handling high-stakes breaches with clarity and confidence
- Overseeing security architecture, compliance, audits, and governance frameworks
- Communicating risk posture to C-suite executives and boards, often translating complex threats into business impact
- Managing cross-functional teams including SOC leads, threat analysts, and compliance officers
Successful CISOs often come from a progression of roles: penetration testing, security architecture, risk consulting, or threat intelligence. Over 10–15 years, they build a blend of:
- Technical credibility (so they can lead engineers)
- Regulatory fluency (so they can navigate audits and compliance)
- Strategic thinking (so they can plan years ahead of evolving threats)
- Executive communication (so they can secure budget, buy-in, and board confidence)
In 2025, the modern CISO is expected to:
- Collaborate with DevOps, cloud, and legal teams on secure digital transformation
- Address AI and deepfake threats, supply chain vulnerabilities, and insider risks
- Adapt to frameworks like Zero Trust, MITRE ATT&CK, and risk-based security budgeting
This role carries pressure but also impact. A CISO doesn’t just protect systems. They protect trust. For those who aspire to lead at the highest levels of cybersecurity, this is the pinnacle and a path worth preparing for.
2. Security Architect
A Security Architect is the strategist behind an organization’s cybersecurity foundation. While security analysts and engineers focus on identifying and responding to threats, the architect is responsible for designing the structures that prevent those threats from succeeding in the first place.
Think of this role as the bridge between technical depth and business reality. The Security Architect must balance what’s secure with what’s scalable and what’s realistic to implement across fast-moving teams.
- Average Salary (India): ₹35–50 LPA
- Average Salary (Global): $130,000–$200,000/year
Key responsibilities include:
- Designing the end-to-end security architecture across applications, networks, cloud, and endpoints
- Developing policies, protocols, and standards that ensure long-term security without disrupting operations
- Evaluating third-party tools, vendors, and platforms for integration and compliance risks
- Collaborating across IT, DevOps, SOC, and compliance teams to align architecture with business goals
- Building threat models and proactively identifying architecture-level vulnerabilities before deployment
In 2025, the modern Security Architect must also:
- Understand cloud-native environments, including Kubernetes, containers, and microservices
- Build for Zero Trust principles, where access is always verified and segmented
- Incorporate secure-by-design principles into product development and infrastructure planning
- Evaluate API security, CI/CD pipeline hardening, and third-party integrations
What sets this role apart is the mindset. A Security Architect doesn’t just react to threats they think like an attacker in order to design resilient systems. They’re part engineer, part strategist, and part risk advisor.
This is an ideal role for those who enjoy building at scale, collaborating across departments, and creating frameworks that hold up under pressure. It requires strong hands-on experience in systems, networking, and application security often with a background in roles like security engineering, penetration testing, or systems architecture.
3. Ethical Hacker / Penetration Tester
Ethical hackers also known as penetration testers or “red team” operators play a vital role in proactive cybersecurity. Their job is simple in principle but complex in execution: think like a hacker to beat the hacker.
They simulate real-world attacks across systems, networks, and applications to find vulnerabilities before malicious actors do. Unlike attackers, ethical hackers have permission and a mission to improve security by exposing weaknesses responsibly.
- Average Salary (India): ₹12–30 LPA
- Average Salary (Global): $90,000–$150,000/year
Daily responsibilities include:
- Running vulnerability scans on internal and external systems
- Exploiting misconfigurations or insecure endpoints to assess risk
- Conducting phishing simulations and social engineering tests
- Testing APIs, cloud environments, mobile apps, and internal networks
- Writing detailed reports with findings, risk ratings, and remediation guidance
Top tools of the trade:
- Kali Linux, Burp Suite, Nmap, Metasploit, Wireshark, Hydra, SQLmap
- Cloud testing tools like ScoutSuite, Pacu, and AWS CLI-based scripts
- Custom-built payloads and scripts in Python, Bash, or PowerShell
To grow in this role, ethical hackers often pursue certifications such as:
- CEH (Certified Ethical Hacker) – foundational, widely recognized
- OSCP (Offensive Security Certified Professional) – hands-on, rigorous, respected globally
- CPT (Certified Penetration Tester) or eJPT (Junior Penetration Tester) – great for newcomers
In 2025, ethical hackers are expanding into:
- Cloud pentesting: AWS, Azure, and GCP infrastructure assessments
- API and microservice testing: ensuring DevOps and SaaS apps are secure
- Red teaming: multi-step attack simulation that mirrors advanced persistent threats
- AI system security: testing ML models, prompt injection vulnerabilities, and LLM misuse
What makes this role unique is the mindset. Ethical hackers are problem-solvers who:
- Thrive in uncertainty and enjoy thinking like adversaries
- Are constantly learning because threats and tools evolve fast
- Work across industries from banking and defense to SaaS and healthcare
If you enjoy breaking systems to make them better, ethical hacking is a high-impact, high-growth career. It’s where curiosity meets responsibility and where your ability to think critically can prevent real-world damage.
4. Cloud Security Engineer
As businesses shift their infrastructure to platforms like AWS, Microsoft Azure, and Google Cloud, the need for specialized security in the cloud has exploded. Cloud Security Engineers are the architects and guardians of that transformation. Their mission: to ensure every piece of infrastructure from storage to APIs is secure by design and resilient in practice.
In 2025, this role sits at the heart of digital operations. It requires not only technical depth but also a deep understanding of cloud architecture, automation, and real-time threat response.
- Average Salary (India): ₹18–35 LPA
- Average Salary (Global): $110,000–$180,000/year
Core responsibilities include:
- Implementing Identity and Access Management (IAM) policies that define who can do what, and from where
- Encrypting data at rest and in transit, ensuring both compliance and resilience
- Integrating DevSecOps practices, embedding security into CI/CD pipelines
- Securing containers and serverless functions, particularly in Kubernetes and microservices architectures
- Monitoring infrastructure in real-time using tools like AWS Security Hub, Azure Sentinel, and GCP Security Command Center
Tools and frameworks you’ll often work with:
- Terraform, CloudFormation, and Pulumi for infrastructure as code (IaC)
- AWS Config, Azure Defender, GCP Forseti for configuration auditing
- SIEM tools like Splunk, Sumo Logic, and ELK for incident detection
- Cloud-native firewalls, WAFs, and key management systems (KMS)
In 2025, the most in-demand cloud security engineers also:
- Understand multi-cloud environments and know how to standardize security across providers
- Apply Zero Trust principles, ensuring continuous verification of identity and device posture
- Collaborate with developers and DevOps engineers to design “secure by default” systems
- Stay updated on cloud misconfiguration trends, API threats, and compliance frameworks like ISO 27001, SOC 2, and GDPR
This role is ideal for those who enjoy automation, scalability, and solving problems at the infrastructure level. It requires both hands-on cloud experience and a security-first mindset especially in environments where downtime or breach could cost millions.
For professionals aiming to specialize, relevant certifications include:
- CCSP (Certified Cloud Security Professional) – vendor-neutral and management-focused
- AWS Certified Security – Specialty – focused on best practices and threat modeling within AWS
- GCP Professional Cloud Security Engineer – critical for projects on Google Cloud
- AZ-500 – Microsoft’s certification for Azure Security Engineers
In a world where nearly every digital product lives in the cloud, cloud security isn’t just a technical necessity it’s a strategic advantage. For those with the skills to protect it, the career outlook is not just strong it’s essential.
5. Incident Response Manager / SOC Lead
When cyber incidents strike and they will it’s the Incident Response Manager who steps in to contain the chaos. Often leading a Security Operations Center (SOC) or a specialized response team, this role demands a unique blend of technical expertise, decision-making under pressure, and cross-team coordination.
In 2025, as attacks become faster, stealthier, and AI-assisted, response time is everything. This role doesn’t just fix problems it minimizes damage, preserves evidence, and ensures business continuity.
- Average Salary (India): ₹20–40 LPA
- Average Salary (Global): $100,000–$160,000/year
Key responsibilities include:
- Leading incident detection and response efforts during live security events
- Coordinating across teams network, application, legal, PR to ensure fast containment and accurate communication
- Conducting forensic analysis to trace the source, scope, and method of the breach
- Building and updating playbooks for various attack scenarios (ransomware, DDoS, insider threats)
- Performing post-incident reviews to improve systems and prepare for future threats
Tools and platforms commonly used:
- SIEM tools like Splunk, IBM QRadar, LogRhythm, and Sumo Logic
- Endpoint Detection and Response (EDR) platforms like CrowdStrike, SentinelOne, and Microsoft Defender
- Threat intelligence feeds to map Indicators of Compromise (IOCs) in real time
- Digital forensics tools such as FTK, EnCase, and Volatility
- SOAR platforms to automate repetitive tasks and speed up triage
What sets this role apart:
- It’s both technical and operational you need to understand packet captures and know how to brief an executive
- It requires real-time thinking under pressure often when the stakes are at their highest
- You must be able to distinguish signal from noise, focusing on the real threats and ignoring the false alarms
The best Incident Response Managers often come from roles like SOC Analyst, Threat Hunter, or Malware Analyst. Over time, they develop:
- A deep understanding of attacker behavior and tactics
- Familiarity with regulatory reporting and legal implications of breaches
- A calm, methodical approach to high-pressure situations
In 2025, response teams must also prepare for:
- AI-generated malware that mutates mid-attack
- Multi-cloud breaches involving multiple platforms and data silos
- Insider threats where behavior is harder to model
- Business continuity challenges, where downtime affects revenue and trust instantly
If you’re the kind of person who stays calm under pressure, thrives on pattern analysis, and wants to lead from the front lines, this is one of the most impactful roles in cybersecurity today.
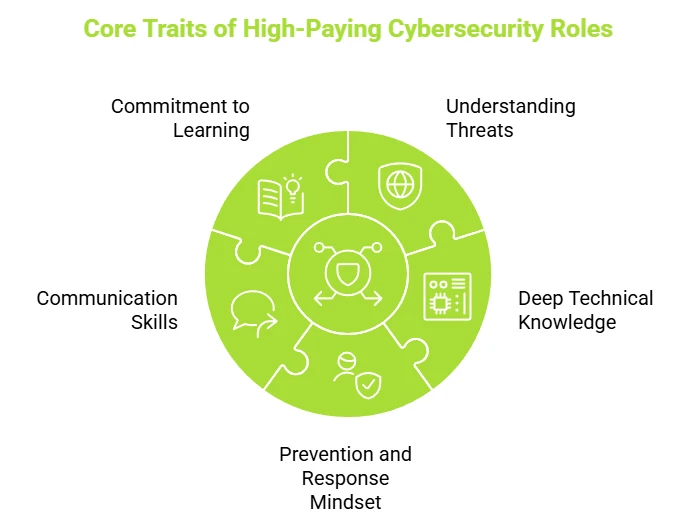
What These Roles Have in Common
While the specializations differ, these high-paying roles share some core traits:
- A strong understanding of real-world threats and how attackers operate
- Deep knowledge of systems, networks, or applications, and how to protect them
- A mindset focused on prevention, response, and adaptability
- The ability to communicate risks clearly to both technical and non-technical teams
- A commitment to learning, as the threat landscape evolves, so must your skills
These roles aren’t just jobs, they’re missions. Each one plays a critical part in shaping the future of digital trust and resilience.
How Appin Helps You Build Toward These Roles
At Appin, you don’t just learn theory, you practice in real environments. Whether you’re aiming for penetration testing, cloud security, or leadership tracks, our programs help you build real capabilities that align with the industry’s highest-paying opportunities.
- Hands-on labs that simulate real attacks and defenses
- Certifications mapped to global job roles like CEH, OSCP, and AWS Security
- Project-based learning that develops both skill and confidence
- Mentorship from cybersecurity professionals working in the field today
Cybersecurity isn’t just growing, it’s paying well for those who are prepared. At Appin, that preparation starts with action. Enquire Now to explore the right learning path for your career goals.


